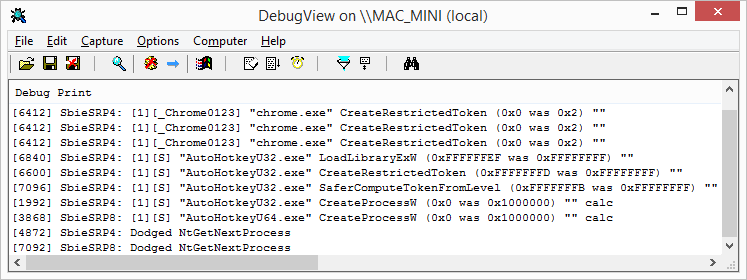
What is new...
Code: Select all
; Toggle build architecture
PtrSize fix 4 ; 32-bit
;PtrSize fix 8 ; 64-bit
; Toggle
;OutputDebug equ 0
OutputDebug equ 1
PtrSizeAsc='0'+PtrSize
SbieSRP_dll equ 'SbieSRP',PtrSizeAsc,'.dll'
match =4,PtrSize{format PE GUI 4.0 DLL}
match =8,PtrSize{format PE64 GUI 5.0 DLL}
entry DllEntryPoint
match =4,PtrSize{include 'WIN32WXP.INC'}
match =8,PtrSize{include 'WIN64WXP.INC'}
; BUCKAROO's trivial customization to fasmw17139\INCLUDE\MACRO\*
; Macroinstructions for making import section (32-bit or 64-bit)
macro import name,[label,string]
{
common
if PtrSize=4
rb (- rva $) and 3
else if PtrSize=8
rb (- rva $) and 7
end if
if defined name#.referred
name#.lookup:
forward
if used label
if string eqtype ''
local _label
if PtrSize=4
dd RVA _label
else if PtrSize=8
dq RVA _label
end if
else
if PtrSize=4
dd 80000000h + string
else if PtrSize=8
dq 8000000000000000h + string
end if
end if
end if
common
if $ > name#.lookup
name#.redundant = 0
if PtrSize=4
dd 0
else if PtrSize=8
dq 0
end if
else
name#.redundant = 1
end if
name#.address:
forward
if used label
if string eqtype ''
if PtrSize=4
label dd RVA _label
else if PtrSize=8
label dq RVA _label
end if
else
if PtrSize=4
label dd 80000000h + string
else if PtrSize=8
label dq 8000000000000000h + string
end if
end if
end if
common
if ~ name#.redundant
if PtrSize=4
dd 0
else if PtrSize=8
dq 0
end if
end if
forward
if used label & string eqtype ''
_label dw 0
label#.ansi:
db string,0
rb RVA $ and 1
end if
common
end if
}
match =4,PtrSize
{
dbz equ dd
tax equ eax
tcx equ ecx
tdx equ edx
}
match =8,PtrSize
{
dbz equ dq
tax equ rax
tcx equ rcx
tdx equ rdx
;
;tcx equ r10
;tdx equ r11
}
macro mioli op1*
{
mov op1,tax
}
macro sioli op1*
{
mov tax,op1
}
macro tioli
{
test tax,tax
}
struc UNICODE_STRING
{
.Length dw ?
.MaximumLength dw ?
if PtrSize=8
rb 4
end if
.Buffer dbz ?
}
virtual at 0
UNICODE_STRING UNICODE_STRING
end virtual
macro m_lp [m]
{
m dbz ?
}
struc ntdll_
{
m_lp .LdrLoadDll,.NtGetNextProcess
}
struc kernel32_
{
m_lp .CreateProcessW,.LoadLibraryExW
}
struc kernelbase_
{
m_lp .LoadLibraryExW
}
struc advapi32_
{
m_lp .CreateRestrictedToken,.SaferComputeTokenFromLevel
}
struc SbieApi_
{
m_lp .EnumProcessEx,.QueryProcess
}
struc SbieDll_
{
m_lp .Hook
}
struc SbieDll_dll_
{
.SbieApi_EnumProcessEx db 'SbieApi_EnumProcessEx',0
.SbieApi_QueryProcess db 'SbieApi_QueryProcess',0
.SbieDll_Hook db 'SbieDll_Hook',0
}
!LOAD_IGNORE_CODE_AUTHZ_LEVEL=not 0x10
!SANDBOX_INERT=not 0x2
!SAFER_TOKEN_MAKE_INERT=not 0x4
!CREATE_BREAKAWAY_FROM_JOB=not 0x1000000
section '.data' data readable writeable
;[pid]
; SbieSRPx: [session_id][box_name] "image_name" ProcName (flags was flags) "FileName" CommandLine
szDbgInfoFmt du '%hs: %ls%hs',10,0
szDbgHookFmt du '%hs: [%d][%ls] "%ls" %hs (0x%X was 0x%X) "%ls" %ls',10,0
szSbieSRP db 'SbieSRP',PtrSizeAsc,0
ntdll_dll db 'ntdll.dll',0
NtGetNextProcess.ansi db 'NtGetNextProcess',0
kernel32_dll db 'kernel32.dll',0
kernelbase_dll db 'kernelbase.dll',0
LoadLibraryExW.ansi db 'LoadLibraryExW',0
align 16
process_id dbz ?
struc _ProcessQuery
{
.box_name rw 34
.image_name rw 96
.sid_string rw 96
.session_id dd ?
}
HithertoProcess _ProcessQuery
ntdll ntdll_
kernel32 kernel32_
kernelbase kernelbase_
advapi32 advapi32_
SbieApi SbieApi_
SbieDll SbieDll_
SbieDll_dll SbieDll_dll_
section '.text' code executable readable
proc DllEntryPoint hinstDLL,fdwReason,lpvReserved
if PtrSize=8
mov [hinstDLL],rcx
mov [fdwReason],rdx
end if
cmp [fdwReason],DLL_PROCESS_ATTACH
je DLL_PROCESS_ATTACH_DllEntryPoint
cmp [fdwReason],DLL_PROCESS_DETACH
je DLL_PROCESS_DETACH_DllEntryPoint
match =1,OutputDebug{stdcall OutputDebugText,'DllEntryPoint',NULL,NULL,NULL,NULL,NULL}
jmp @f
DLL_PROCESS_ATTACH_DllEntryPoint:
match =1,OutputDebug{stdcall OutputDebugText,'DLL_PROCESS_ATTACH',NULL,NULL,NULL,NULL,NULL}
invoke DisableThreadLibraryCalls,[hinstDLL]
jmp @f
DLL_PROCESS_DETACH_DllEntryPoint:
match =1,OutputDebug{stdcall OutputDebugText,'DLL_PROCESS_DETACH',NULL,NULL,NULL,NULL,NULL}
jmp @f
@@:
sioli TRUE
ret
endp
proc detour_LoadLibraryExW lpFileName,hFile,dwFlags
locals
match =4,PtrSize{dwFlagsOld dd ?}
match =8,PtrSize{dwFlagsOld dq ?}
endl
if PtrSize=8
mov [lpFileName],rcx
mov [hFile],rdx
mov [dwFlags],r8
end if
mov tax,[dwFlags]
mov [dwFlagsOld],tax
and [dwFlags],!LOAD_IGNORE_CODE_AUTHZ_LEVEL
match =0,OutputDebug
{
cmp [dwFlags],tax
je @f
}
stdcall OutputDebugText,NULL,LoadLibraryExW.ansi,[lpFileName],NULL,[dwFlags],[dwFlagsOld]
@@:
invoke kernel32.LoadLibraryExW,[lpFileName],[hFile],[dwFlags]
;invoke kernelbase.LoadLibraryExW,[lpFileName],[hFile],[dwFlags]
ret
endp
proc detour_6_2_LdrLoadDll dwFlags,SearchPathForFile,lpFileNameUnicodeString,hModule
locals
match =4,PtrSize{dwFlagsOld dd ?}
match =8,PtrSize{dwFlagsOld dq ?}
endl
if PtrSize=8
mov [dwFlags],rcx
mov [SearchPathForFile],rdx
mov [lpFileNameUnicodeString],r8
mov [hModule],r9
end if
mov tax,[dwFlags]
mov [dwFlagsOld],tax
and [dwFlags],!LOAD_IGNORE_CODE_AUTHZ_LEVEL
match =0,OutputDebug
{
cmp [dwFlags],tax
je @f
}
mov tdx,[lpFileNameUnicodeString]
cmp tdx,NULL
je @f
;xor tax,tax
xor tcx,tcx
mov ax,[tdx+UNICODE_STRING.MaximumLength]
mov cx,[tdx+UNICODE_STRING.Length]
sub ax,cx
cmp ax,2
jnae @f
mov tdx,[lpFileNameUnicodeString]
mov tdx,[tdx+UNICODE_STRING.Buffer]
cmp word [tdx+tcx],NULL
jne @f
stdcall OutputDebugText,NULL,LdrLoadDll.ansi,tdx,NULL,[dwFlags],[dwFlagsOld]
@@:
invoke ntdll.LdrLoadDll,[dwFlags],[SearchPathForFile],[lpFileNameUnicodeString],[hModule]
ret
endp
; Incorrect prototype - Was a work-in-process, was...
proc detour_5_0_LdrLoadDll SearchPathForFile,dwFlags,lpFileNameUnicodeString,hModule
locals
match =4,PtrSize{dwFlagsOld dd ?}
match =8,PtrSize{dwFlagsOld dq ?}
endl
if PtrSize=8
mov [SearchPathForFile],rcx
mov [dwFlags],rdx
mov [lpFileNameUnicodeString],r8
mov [hModule],r9
end if
mov tax,[dwFlags]
mov [dwFlagsOld],tax
and [dwFlags],!LOAD_IGNORE_CODE_AUTHZ_LEVEL
match =0,OutputDebug
{
cmp [dwFlags],tax
je @f
}
;
@@:
invoke ntdll.LdrLoadDll,[SearchPathForFile],[dwFlags],[lpFileNameUnicodeString],[hModule]
ret
endp
proc detour_CreateRestrictedToken ExistingTokenHandle,Flags,DisableSidCount,SidsToDisable,DeletePrivilegeCount,PrivilegesToDelete,RestrictedSidCount,SidsToRestrict,NewTokenHandle
locals
match =4,PtrSize{FlagsOld dd ?}
match =8,PtrSize{FlagsOld dq ?}
endl
if PtrSize=8
mov [ExistingTokenHandle],rcx
mov [Flags],rdx
mov [DisableSidCount],r8
mov [SidsToDisable],r9
end if
mov tax,[Flags]
mov [FlagsOld],tax
and [Flags],!SANDBOX_INERT
match =0,OutputDebug
{
cmp [Flags],tax
je @f
}
stdcall OutputDebugText,NULL,CreateRestrictedToken.ansi,NULL,NULL,[Flags],[FlagsOld]
@@:
invoke advapi32.CreateRestrictedToken,[ExistingTokenHandle],[Flags],[DisableSidCount],[SidsToDisable],[DeletePrivilegeCount],[PrivilegesToDelete],[RestrictedSidCount],[SidsToRestrict],[NewTokenHandle]
ret
endp
proc detour_SaferComputeTokenFromLevel LevelHandle,InAccessToken,OutAccessToken,dwFlags,lpReserved
locals
match =4,PtrSize{dwFlagsOld dd ?}
match =8,PtrSize{dwFlagsOld dq ?}
endl
if PtrSize=8
mov [LevelHandle],rcx
mov [InAccessToken],rdx
mov [OutAccessToken],r8
mov [dwFlags],r9
end if
mov tax,[dwFlags]
mov [dwFlagsOld],tax
and [dwFlags],!SAFER_TOKEN_MAKE_INERT
match =0,OutputDebug
{
cmp [dwFlags],tax
je @f
}
stdcall OutputDebugText,NULL,SaferComputeTokenFromLevel.ansi,NULL,NULL,[dwFlags],[dwFlagsOld]
@@:
invoke advapi32.SaferComputeTokenFromLevel,[LevelHandle],[InAccessToken],[OutAccessToken],[dwFlags],[lpReserved]
ret
endp
proc detour_CreateProcessW lpApplicationName,lpCommandLine,lpProcessAttributes,lpThreadAttributes,bInheritHandles,dwCreationFlags,lpEnvironment,lpCurrentDirectory,lpStartupInfo,lpProcessInformation
locals
match =4,PtrSize{dwCreationFlagsOld dd ?}
match =8,PtrSize{dwCreationFlagsOld dq ?}
endl
if PtrSize=8
mov [lpApplicationName],rcx
mov [lpCommandLine],rdx
mov [lpProcessAttributes],r8
mov [lpThreadAttributes],r9
end if
mov tax,[dwCreationFlags]
mov [dwCreationFlagsOld],tax
and [dwCreationFlags],!CREATE_BREAKAWAY_FROM_JOB
match =0,OutputDebug
{
cmp [dwCreationFlags],tax
je @f
}
stdcall OutputDebugText,NULL,CreateProcessW.ansi,[lpApplicationName],[lpCommandLine],[dwCreationFlags],[dwCreationFlagsOld]
@@:
invoke kernel32.CreateProcessW,[lpApplicationName],[lpCommandLine],[lpProcessAttributes],[lpThreadAttributes],[bInheritHandles],[dwCreationFlags],[lpEnvironment],[lpCurrentDirectory],[lpStartupInfo],[lpProcessInformation]
ret
endp
proc detour_NtGetNextProcess ProcessHandle,DesiredAccess,HandleAttributes,Flags,NewProcessHandle
stdcall OutputDebugText,'Dodged ',NtGetNextProcess.ansi,NULL,NULL,NULL,NULL
sioli 0x8000001A ; STATUS_NO_MORE_ENTRIES
ret
endp
proc OutputDebugText szInfo,lpProcName,sz1,sz2,dwFlagsNew,dwFlagsOld
locals
match =4,PtrSize{lpOut dd ?}
match =8,PtrSize{lpOut dq ?}
endl
if PtrSize=8
mov [szInfo],rcx
mov [lpProcName],rdx
mov [sz1],r8
mov [sz2],r9
end if
invoke VirtualAlloc,NULL,2050,MEM_COMMIT+MEM_RESERVE,PAGE_READWRITE
mioli [lpOut]
tioli
jz fail_OutputDebugText
cmp [szInfo],NULL
je @f
cinvoke wsprintfW,[lpOut],szDbgInfoFmt,szSbieSRP,[szInfo],[lpProcName]
jmp pass_OutputDebugText
@@:
cinvoke wsprintfW,[lpOut],szDbgHookFmt,szSbieSRP,[HithertoProcess.session_id],HithertoProcess.box_name,HithertoProcess.image_name,[lpProcName],[dwFlagsNew],[dwFlagsOld],[sz1],[sz2]
pass_OutputDebugText:
invoke OutputDebugStringW,[lpOut]
invoke VirtualFree,[lpOut],0,MEM_RELEASE
fail_OutputDebugText:
ret
endp
proc InjectDllMain hSbieDll,UnusedParameter
if PtrSize=8
mov [hSbieDll],rcx
end if
match =1,OutputDebug{stdcall OutputDebugText,'InjectDllMain',NULL,NULL,NULL,NULL,NULL}
invoke GetProcAddress,[hSbieDll],SbieDll_dll.SbieDll_Hook
mioli [SbieDll.Hook]
tioli
jz fail_InjectDllMain
invoke GetProcAddress,[hSbieDll],SbieDll_dll.SbieApi_QueryProcess
mioli [SbieApi.QueryProcess]
tioli
jz fail_InjectDllMain
invoke GetProcAddress,[hSbieDll],SbieDll_dll.SbieApi_EnumProcessEx
mioli [SbieApi.EnumProcessEx]
tioli
jz fail_InjectDllMain
invoke GetCurrentProcessId
mioli [process_id]
invoke SbieApi.QueryProcess,[process_id],HithertoProcess.box_name,HithertoProcess.image_name,HithertoProcess.sid_string,HithertoProcess.session_id
tioli
jnz fail_InjectDllMain
; TODO workaround __COMPAT_LAYER
; invoke GetVersion
; IsWindows8OrGreater
; cmp al,6
; jnae @f
; cmp ah,2
; jnae @f
;stdcall OutputDebugText,'6.2',NULL,NULL,NULL,NULL,NULL
; invoke SbieDll.Hook,LdrLoadDll.ansi,[LdrLoadDll],detour_6_2_LdrLoadDll
; mioli [ntdll.LdrLoadDll]
; jmp past_LdrLoadDll_InjectDllMain
@@:
;stdcall OutputDebugText,'5.0',NULL,NULL,NULL,NULL,NULL
; invoke SbieDll.Hook,LdrLoadDll.ansi,[LdrLoadDll],detour_5_0_LdrLoadDll
; mioli [ntdll.LdrLoadDll]
past_LdrLoadDll_InjectDllMain:
; advapi32.CreateRestrictedToken
invoke SbieDll.Hook,CreateRestrictedToken.ansi,[CreateRestrictedToken],detour_CreateRestrictedToken
mioli [advapi32.CreateRestrictedToken]
; advapi32.SaferComputeTokenFromLevel
invoke SbieDll.Hook,SaferComputeTokenFromLevel.ansi,[SaferComputeTokenFromLevel],detour_SaferComputeTokenFromLevel
mioli [advapi32.SaferComputeTokenFromLevel]
; kernel32.CreateProcessW
invoke SbieDll.Hook,CreateProcessW.ansi,[CreateProcessW],detour_CreateProcessW
mioli [kernel32.CreateProcessW]
@@:
; kernelbase.LoadLibraryExW
invoke GetModuleHandleA,kernelbase_dll
invoke GetProcAddress,tax,LoadLibraryExW.ansi
tioli
jz @f
; invoke SbieDll.Hook,LoadLibraryExW.ansi,tax,detour_LoadLibraryExW
; mioli [kernelbase.LoadLibraryExW]
@@:
; kernel32.LoadLibraryExW
invoke GetModuleHandleA,kernel32_dll
invoke GetProcAddress,tax,LoadLibraryExW.ansi
tioli
jz @f
invoke SbieDll.Hook,LoadLibraryExW.ansi,tax,detour_LoadLibraryExW
mioli [kernel32.LoadLibraryExW]
@@:
; ntdll.NtGetNextProcess
invoke GetModuleHandleA,ntdll_dll
invoke GetProcAddress,tax,NtGetNextProcess.ansi
tioli
jz @f
invoke SbieDll.Hook,NtGetNextProcess.ansi,tax,detour_NtGetNextProcess
mioli [ntdll.NtGetNextProcess]
@@:
match =1,OutputDebug{stdcall OutputDebugText,'Inject stage passed.',NULL,NULL,NULL,NULL,NULL}
ret
fail_InjectDllMain:
stdcall OutputDebugText,'Inject stage failed.',NULL,NULL,NULL,NULL,NULL
ret
endp
section '.idata' data readable import
library ntdll_dll,'ntdll.dll',kernel32_dll,'kernel32.dll',advapi32_dll,'advapi32.dll',user32_dll,'user32.dll'
import ntdll_dll,\
LdrLoadDll,'LdrLoadDll'
import kernel32_dll,\
CreateProcessW,'CreateProcessW',\
DisableThreadLibraryCalls,'DisableThreadLibraryCalls',GetCurrentProcessId,'GetCurrentProcessId',\
GetModuleHandleA,'GetModuleHandleA',GetProcAddress,'GetProcAddress',GetProcessId,'GetProcessId',\
OutputDebugStringW,'OutputDebugStringW',\
VirtualAlloc,'VirtualAlloc',VirtualFree,'VirtualFree'
import advapi32_dll,\
CreateRestrictedToken,'CreateRestrictedToken',SaferComputeTokenFromLevel,'SaferComputeTokenFromLevel'
import user32_dll,\
wsprintfW,'wsprintfW' ;,wvsprintfW,'wvsprintfW'
section '.edata' data readable export
export SbieSRP_dll,InjectDllMain,'InjectDllMain'
section '.reloc' data discardable readable fixups
postpone
{
display '@',10
display ':: INSTALL FROM AN ELEVATED COMMAND PROMPT',10
display 'COPY /B /Y "SbieSRP.dll" "%CommonProgramFiles%\',SbieSRP_dll,'"',10
display '@',10
display 'ATTRIB +R "%CommonProgramFiles%\',SbieSRP_dll,'"',10
display '@',10
display 'SET "Sbie=%ProgramFiles%\Sandboxie"',10
display 'SET "SbieIni="%Sbie%\SbieIni.exe""',10
display '%SbieIni% append GlobalSettings InjectDll "%CommonProgramFiles%\SbieSRP4.dll"',10
display '%SbieIni% append GlobalSettings InjectDll64 "%CommonProgramFiles%\SbieSRP8.dll"',10
display '@'
}
Am not providing support, consider the project abandoned.