 |
Trust No Program |
|
|
Sandboxie Control > Sandbox Settings > Resource Access
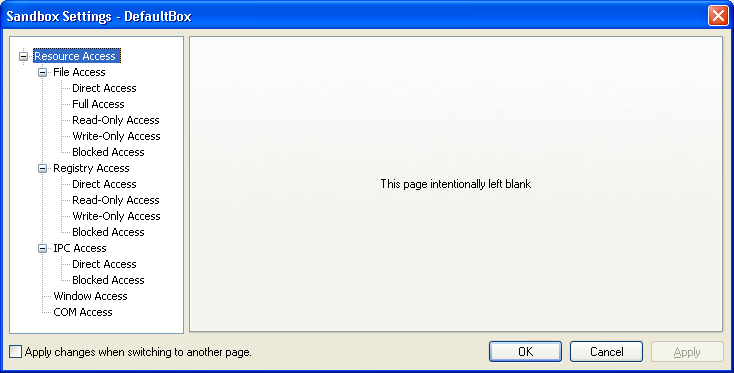
Programs that run in a sandbox are generally not allowed to access system resources directly. In some cases, it may be desirable to make exceptions to this rule. The settings here display and change that set of exceptions.
Examples where exceptions are convenient or necessary:
|
Configuration changes do not apply to programs that are already running sandboxed at the time the configuration is changed. To keep things simple, you are advised to make configuration changes when no programs are running in the sandbox. |
Each settings page within the Resource Access group generally has the following characteristics:
Sandboxie Control > Sandbox Settings > Resource Access > File Access
This category manages the following types of resources: Files, folders, drives, and other devices.
See General Information above for more information about editing resources and associating resources with particular programs.
File Access > Direct Access
Allow direct access to some file or folder, bypassing the supervision of Sandboxie. For example, if you add a folder C:\Downloads, then a program running under Sandboxie will be able to create or update files in that folder.
Note that Direct Access exclusions do not apply when the program itself resides in the sandbox. For example, suppose that you allow direct access to a C:\Downloads folder, and then you go on to install a new Web browser into the sandbox. This new sandboxed browser will not have direct access to the C:\Downloads folder.
Related Sandboxie Ini settings: OpenFilePath
File Access > Full Access
Similar to Direct Access, but always applies, even if the sandboxed program itself resides in the sandbox. For better protection, you are advised to use Direct Access rather than Full Access whenever possible.
Related Sandboxie Ini settings: OpenPipePath
File Access > Read-Only Access
This access mode excludes the effects of sandboxing on a file (or folder) resource, while allowing a program to read, but not modify, the real resource.
Related Sandboxie Ini settings: ReadFilePath
File Access > Write-Only Access
This access mode hides all files and folders which are located within the selected folder outside the sandbox. However, programs in the sandbox can create new files within the corresponding folder in the sandbox.
This setting can only be used effectively on folders. If a file is selected, the effect is the same as the Blocked Access setting (see below).
Related Sandboxie Ini settings: WriteFilePath
File Access > Blocked Access
Deny all access to the resource, for example to a folder containing sensitive data. Blocked Access settings take precedence over all other resource access rules. For example, if an exclusion for C:\Downloads appears in both Direct Access and Blocked Access, the latter will apply, denying all access to the folder.
Related Sandboxie Ini settings: ClosedFilePath
Sandboxie Control > Sandbox Settings > Resource Access > Registry Access
This category manages registry key resources. The registry is a mechanism provided by Windows for programs to store configuration and settings.
See General Information above for more information about editing resources and associating resources with particular programs.
Registry Access > Direct Access
Allow direct access to a registry key resource. Note that Direct Access exclusions do not apply when the program itself resides in the sandbox. This is described in more detail in the File Access category above. Note that unlike in the File Access category, there is no Full Access access mode for registry keys.
Related Sandboxie Ini settings: OpenKeyPath
Registry Access > Read-Only Access
This access mode excludes the effects of sandboxing on a registry key resource, while allowing a program to read, but not modify, the real resource.
Related Sandboxie Ini settings: ReadKeyPath
Registry Access > Write-Only Access
This access mode hides all registry data which is located within the selected registry key outside the sandbox. However, programs in the sandbox can create new registry data within the corresponding folder in the sandbox.
Related Sandboxie Ini settings: WriteKeyPath
Registry Access > Blocked Access
Deny all access to a registry key resource, for example to a key containing Windows policy settings. Blocked Access settings take precedence over all other resource access rules. For example, if an exclusion for a registry key appears in both Direct Access and Blocked Access, the latter will apply, denying all access to the registry key.
Related Sandboxie Ini settings: ClosedKeyPath
Sandboxie Control > Sandbox Settings > Resource Access > IPC Access
This category manages exclusions for NT IPC objects. These resources are created by programs running the system as a way to coordinate operations or otherwise communicate.
See General Information above for more information about editing resources and associating resources with particular programs.
IPC Access > Direct Access
Allow direct access to an IPC object resource. Note that unlike in the File Access and Registry Access categories, Direct Access exclusions for IPC objects always apply to all sandboxed programs.
Related Sandboxie Ini settings: OpenIpcPath
IPC Access > Blocked Access
Deny all access to an IPC object resource. Blocked Access settings take precedence over all other resource access rules. For example, if an exclusion for an IPC object appears in both Direct Access and Blocked Access, the latter will apply, denying all access to the object.
This setting can be used to override default IPC Access > Direct Access settings in Sandboxie, and block the access. For example, by default Sandboxie allows sandboxed programs to access the audio device. To override this and cut off audio output by sandboxed programs, add an exclusion for \RPC Control\AudioSrv.
Related Sandboxie Ini settings: ClosedIpcPath
Sandboxie Control > Sandbox Settings > Resource Access > Window Access
This category manages exclusions for window classes. These resources are primarily related to windows displayed on the screen, but can also be used by programs as a way to coordinate operations or otherwise communicate. You can specify which window classes, that were created outside the sandbox, will be available for use by sandboxed programs.
See General Information above for more information about editing resources and associating resources with particular programs.
Related Sandboxie Ini settings: OpenWinClass
Sandboxie Control > Sandbox Settings > Resource Access > COM Access
This category manages exclusions for COM classes. These resources represent objects which are used as a way to coordinate operations or otherwise communicate. You can specify the COM class identifiers for those COM objects that exist outside the sandbox, and which should be accessible to sandboxed programs.
See General Information above for more information about editing resources and associating resources with particular programs.
Related Sandboxie Ini settings: OpenClsid
Sandboxie is Copyright © 2004-2019 by Sandboxie Holdings, LLC. All rights reserved.
Sandboxie.com | Contact Author